
eufy's recent minimization of a severe security breach as a mere “software bug” significantly underplays the critical exposure of users' personal data and video recordings. Owners of eufy security devices, including eufyCam, Video Doorbell, Floodlight Camera, and Indoor Cam, are urged to take swift action: disconnect your devices, erase your recordings, update your passwords, and sign out of all accounts immediately.
Contents
The Seriousness of the eufy Security Breach
This breach is far from minor – it has potentially given strangers access to your video recordings, contact information, and the names of your cameras. Disconcertingly, eufy has not taken adequate steps to inform its user base directly, despite having their contact details for marketing purposes. One would expect a company in this situation to force a log-out and mandate password changes for all users, yet eufy's response has been disappointingly tepid, raising concerns about their commitment to user privacy and product security.
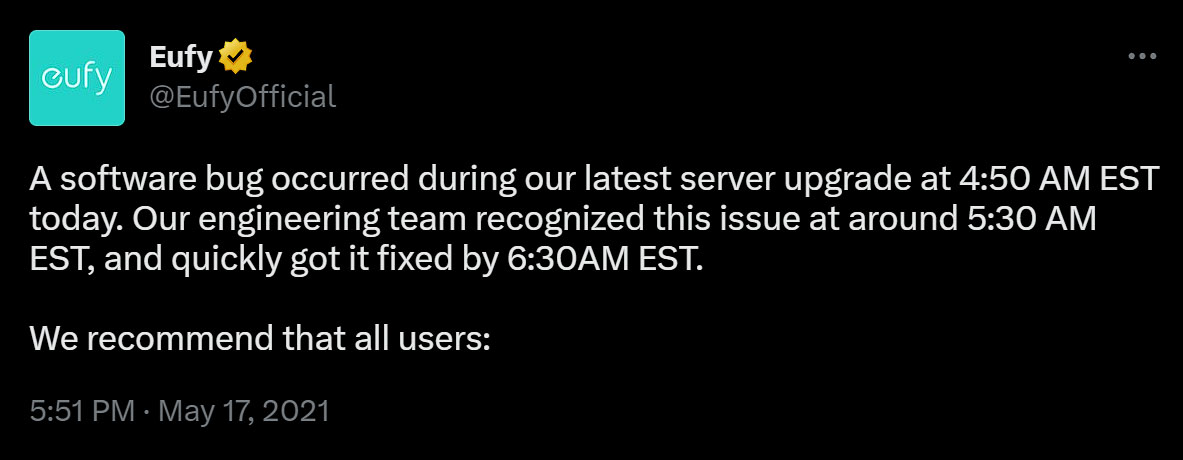
Understanding the eufy Breach
The issue was first highlighted on May 17, 2021, by a Reddit user from New Zealand who stumbled upon footage from another individual's camera, likely located in Australia, along with full access to the Australian user's contact info and camera name. Although this user responsibly refrained from disseminating the footage, the breach could potentially enable less scrupulous individuals to exploit the exposed data.
eufy's acknowledgment of the breach was delayed, coming seven hours after the issue was reported and suspiciously timed after the Reddit post. Their announcement cited a “bug” identified and rectified within two hours, yet failed to provide transparency regarding the breach's scope or the number of affected accounts.
Potential Repercussions for eufy
eufy's lack of comprehensive communication could foreseeably result in significant penalties, especially under regulations like the GDPR, which mandates prompt and clear reporting of data breaches. The GDPR's stringent requirements could subject eufy to fines reaching up to €20 million or 4% of their annual global turnover, whichever is higher. Considering eufy's current approach, such penalties could be deemed justifiable.
1 In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons.
2 Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay.
Art. 33 GDPR

The Argument for Offline Security
Post-breach, there's a growing chorus advising the disconnection of security cameras, especially those kept within the home, from the internet. While logical, such advice may not be feasible for everyone, particularly those less technologically inclined or without the capability to set up local storage solutions. Companies like eufy not offering comprehensive, open APIs further complicates the situation, pushing consumers towards potentially insecure cloud-based services.
Despite the wisdom of hindsight, such advice offers little solace to those currently impacted by eufy's breach. Therefore, the immediate recommendation remains: Disconnect your eufy security devices, delete all stored recordings, update your passwords, and log out of your accounts without delay. Moreover, consider ceasing further investment in eufy products until they demonstrably prioritize user security and data protection.

The security issue is one thing, but I had a horrible experience trying to install and use eufy 2C cameras and homebase 2 and decided to send them back and uninstall my phone app and the PC app, running on Win11 OS. I could uninstall the phone app, with no problem, but removing the app from the PC that’s an entirely different situation. So far couldn’t find the files anywhere on my computer; searched in Win “add or remove programs”, and the extensions in Firefox and Chrome to no avail.
Google is of no help either. Do you have any ideas about what to do?
Thanks.
Regards,
Kris